
Airways, fee processors, 911 name facilities, TV networks, and different companies have been scrambling this morning after a buggy replace to CrowdStrike’s Falcon safety software program induced Home windows-based programs to crash with a dreaded blue display screen of loss of life (BSOD) error message.
We’re updating our story concerning the outage with new particulars as now we have them. Microsoft and CrowdStrike each say that “the affected replace has been pulled,” so what’s most essential for IT admins within the quick time period is getting their programs again up and operating once more. In accordance with steerage from Microsoft, fixes vary from annoying however straightforward to extremely time-consuming and sophisticated, relying on the variety of programs you need to repair and the best way your programs are configured.
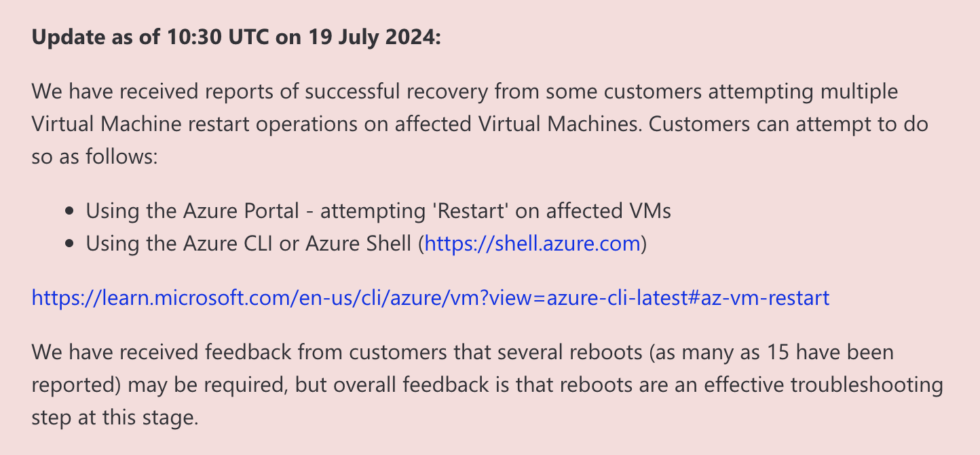
Microsoft’s Azure standing web page outlines a number of fixes. The primary and best is just to attempt to reboot affected machines time and again, which provides affected machines a number of probabilities to attempt to seize CrowdStrike’s non-broken replace earlier than the dangerous driver could cause the BSOD. Microsoft says that a few of its clients have needed to reboot their programs as many as 15 occasions to tug down the replace.
Microsoft
If rebooting doesn’t work
If rebooting a number of occasions is not fixing your downside, Microsoft recommends restoring your programs utilizing a backup from earlier than 4:09 UTC on July 18 (simply after midnight on Friday, Japanese time), when CrowdStrike started pushing out the buggy replace. Crowdstrike says a reverted model of the file was deployed at 5:27 UTC.
If these easier fixes do not work, it’s possible you’ll have to boot your machines into Secure Mode so you’ll be able to manually delete the file that is inflicting the BSOD errors. For digital machines, Microsoft recommends attaching the digital disk to a known-working restore VM so the file might be deleted, then reattaching the digital disk to its authentic VM.
The file in query is a CrowdStrike driver situated at Home windows/System32/Drivers/CrowdStrike/C-00000291*.sys. As soon as it is gone, the machine ought to boot usually and seize a non-broken model of the driving force.
Deleting that file on every one in all your affected programs individually is time-consuming sufficient, nevertheless it’s even extra time-consuming for patrons utilizing Microsoft’s BitLocker drive encryption to guard knowledge at relaxation. Earlier than you’ll be able to delete the file on these programs, you will want the restoration key that unlocks these encrypted disks and makes them readable (usually, this course of is invisible, as a result of the system can simply learn the important thing saved in a bodily or digital TPM module).
This could trigger issues for admins who aren’t utilizing key administration to retailer their restoration keys, since (by design!) you’ll be able to’t entry a drive with out its restoration key. If you do not have that key, Cryptography and infrastructure engineer Tony Arcieri on Mastodon in contrast this to a “self-inflicted ransomware assault,” the place an attacker encrypts the disks in your programs and withholds the important thing till they receives a commission.
And even if you happen to do have a restoration key, your key administration server may additionally be affected by the CrowdStrike bug.
We’ll proceed to trace suggestions from Microsoft and CrowdStrike about fixes as every firm’s respective standing pages are up to date.
“We perceive the gravity of the state of affairs and are deeply sorry for the inconvenience and disruption,” wrote CrowdStrike CEO George Kurtz on X, previously Twitter. “We’re working with all impacted clients to make sure that programs are again up and so they can ship the companies their clients are relying on.”




