[ad_1]
JAVS
A software program maker serving greater than 10,000 courtrooms all through the world hosted an utility replace containing a hidden backdoor that maintained persistent communication with a malicious web site, researchers reported Thursday, within the newest episode of a supply-chain assault.
The software program, often known as the JAVS Viewer 8, is a element of the JAVS Suite 8, an utility bundle courtrooms use to file, play again, and handle audio and video from proceedings. Its maker, Louisville, Kentucky-based Justice AV Options, says its merchandise are utilized in greater than 10,000 courtrooms all through the US and 11 different international locations. The corporate has been in enterprise for 35 years.
JAVS Viewer customers at excessive threat
Researchers from safety agency Rapid7 reported {that a} model of the JAVS Viewer 8 obtainable for obtain on javs.com contained a backdoor that gave an unknown menace actor persistent entry to contaminated gadgets. The malicious obtain, planted inside an executable file that installs the JAVS Viewer model 8.3.7, was obtainable no later than April 1, when a submit on X (previously Twitter) reported it. It’s unclear when the backdoored model was faraway from the corporate’s obtain web page. JAVS representatives didn’t instantly reply to questions despatched by electronic mail.
“Customers who’ve model 8.3.7 of the JAVS Viewer executable put in are at excessive threat and may take fast motion,” Rapid7 researchers Ipek Solak, Thomas Elkins, Evan McCann, Matthew Smith, Jake McMahon, Tyler McGraw, Ryan Emmons, Stephen Fewer, and John Fenninger wrote. “This model accommodates a backdoored installer that permits attackers to achieve full management of affected methods.”
The installer file was titled JAVS Viewer Setup 8.3.7.250-1.exe. When executed, it copied the binary file fffmpeg.exe to the file path C:Program Information (x86)JAVSViewer 8. To bypass safety warnings, the installer was digitally signed, however with a signature issued to an entity referred to as “Vanguard Tech Restricted” relatively than to “Justice AV Options Inc.,” the signing entity used to authenticate respectable JAVS software program.
fffmpeg.exe, in flip, used Home windows Sockets and WinHTTP to determine communications with a command-and-control server. As soon as efficiently related, fffmpeg.exe despatched the server passwords harvested from browsers and information in regards to the compromised host, together with hostname, working system particulars, processor structure, program working listing, and the person identify.
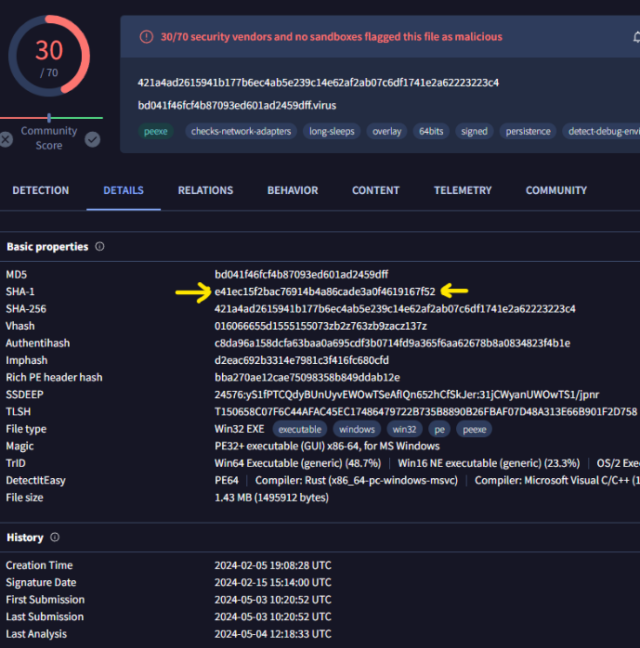
The researchers stated fffmpeg.exe additionally downloaded the file chrome_installer.exe from the IP tackle 45.120.177.178. chrome_installer.exe went on to execute a binary and a number of other Python scripts that have been chargeable for stealing the passwords saved in browsers. fffmpeg.exe is related to a recognized malware household referred to as GateDoor/Rustdoor. The exe file was already flagged by 30 endpoint safety engines.
Rapid7
The variety of detections had grown to 38 on the time this submit went stay.
The researchers warned that the method of disinfecting contaminated gadgets would require care. They wrote:
To remediate this problem, affected customers ought to:
- Reimage any endpoints the place JAVS Viewer 8.3.7 was put in. Merely uninstalling the software program is inadequate, as attackers could have implanted further backdoors or malware. Re-imaging supplies a clear slate.
- Reset credentials for any accounts that have been logged into affected endpoints. This contains native accounts on the endpoint itself in addition to any distant accounts accessed in the course of the interval when JAVS Viewer 8.3.7 was put in. Attackers could have stolen credentials from compromised methods.
- Reset credentials utilized in net browsers on affected endpoints. Browser periods could have been hijacked to steal cookies, saved passwords, or different delicate info.
- Set up the newest model of JAVS Viewer (8.3.8 or larger) after re-imaging affected methods. The brand new model doesn’t include the backdoor current in 8.3.7.
Fully re-imaging affected endpoints and resetting related credentials is essential to make sure attackers haven’t continued by means of backdoors or stolen credentials. All organizations working JAVS Viewer 8.3.7 ought to take these steps instantly to deal with the compromise.
The Rapid7 submit included an announcement from JAVS that confirmed that the installer for model 8.3.7 of the JAVS viewer was malicious.
“We pulled all variations of Viewer 8.3.7 from the JAVS web site, reset all passwords, and performed a full inside audit of all JAVS methods,” the assertion learn. “We confirmed all at the moment obtainable information on the JAVS.com web site are real and malware-free. We additional verified that no JAVS Supply code, certificates, methods, or different software program releases have been compromised on this incident.”
The assertion didn’t clarify how the installer grew to become obtainable for obtain on its web site. It additionally did not say if the corporate retained an outdoor agency to research.
The incident is the newest instance of a supply-chain assault, a method that tampers with a respectable service or piece of software program with the purpose of infecting all downstream customers. These kinds of assaults are often carried out by first hacking the supplier of the service or software program. There’s no certain method to forestall falling sufferer to supply-chain assaults, however one doubtlessly helpful measure is to vet a file utilizing VirusTotal earlier than executing it. That recommendation would have served JAVS customers effectively.
[ad_2]